Court Recordings Exposed in Qilin Ransomware Attack on Victoria’s Court System

Australia’s Court Services Victoria (CSV), the independent statutory authority managing the state’s court systems, has confirmed a Qilin ransomware attack that exposed sensitive video recordings of court hearings. In a statement published today, CSV revealed the cyber incident, detected on December 21, 2023, disrupted operations and granted unauthorized access to its audio-visual archive. Cybersecurity Breach […]
Kansas Courts Still Offline After Security Incident

Information systems of state courts across Kansas are still offline after they’ve been disrupted in what the Kansas judicial branch described last Thursday as a “security incident.” The incident has affected a wide range of systems, including the Kansas Courts eFiling system, the electronic payments system, and the case management systems employed by district and […]
Google Makes Passkeys the Default Sign-in Option
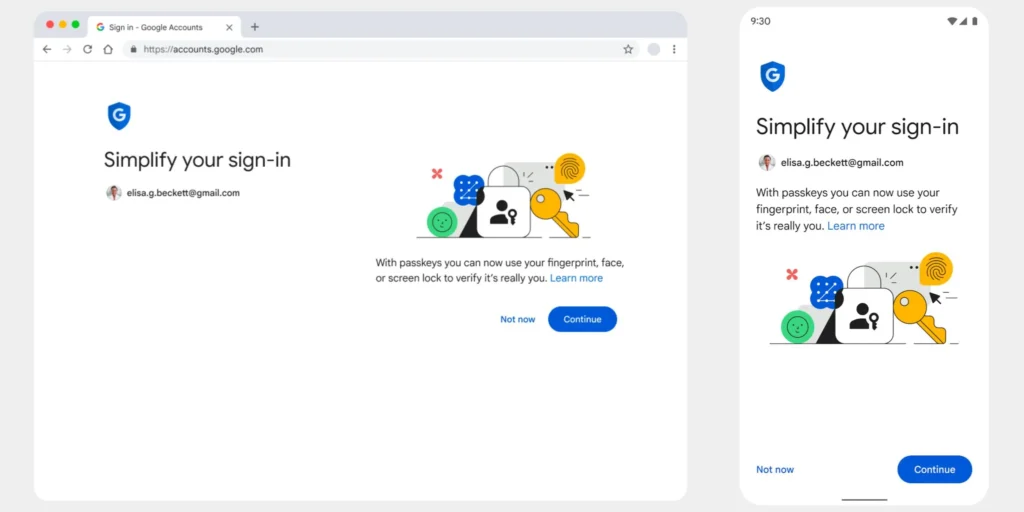
Google announced today that from now on, passkeys are the default sign-in option across all personal Google Accounts. This means that users can now sign in to their accounts without entering a password or using 2-Step Verification (2SV) when logging in. Read: Google Enables Real-Time Phishing Protection for All Chrome Users Google announced that passkeys […]
Ransomware Groups Dominating 2023: What You Need to Know

Ransomware is a type of malicious software that encrypts the victim’s data and demands a ransom for its decryption. Ransomware attacks have been on the rise in recent years, affecting businesses, governments, and individuals alike. In 2023, ransomware groups are dominating the cybercrime landscape, using sophisticated techniques and tactics to evade detection and extort their […]
Cybersecurity Indicators and Tools to Measure the Impact on The Company

Cybersecurity is essential for businesses of all sizes. It helps to protect data, assets, and reputation from cyberattacks. But how can businesses measure the impact of their cybersecurity efforts? Organizations can use cybersecurity indicators and tools to learn more. Indicators of Cybersecurity Impact There are a number of indicators and tools that can be used […]
GitHub steps up security for active developers – 2FA requirement coming soon

GitHub, the world’s largest cloud-based provider of software development tools and services, announced that it will soon make two-factor authentication (2FA) mandatory for active developers. Starting next week, any developer who wants to access their account at GitHub must set up 2FA to continue using the service. Read: The FBI is investigating a data breach […]
Colombian Company Audifarma Suffers Cyberattack

Audifarma, one of the largest drugstore chains in Latin America, recently suffered an external cyberattack that forced them to disable their physical and virtual servers to protect the organization’s and users’ information, taking their website and app are also out of service. This article will explain the details of the attack, the response from Audifarma, […]
How to shop online safely?

This December, everything revolves around family, friends, sharing and, of course, shopping of many kinds. In recent years, the latter have changed to have a great presence in the digital world. Websites, social networks, and even email have created a whole area called e-commerce. But to be sure that each transaction is carried out safely, […]
Passwords are becoming more insecure

There is always talk in the cybersecurity area about passwords since each platform asks us to have one, and it is recommended that they be different; never use the same one in two places. But, as technology advances, so do the ways to steal passwords. That’s why experts are looking for ways to know their […]
Twitter faces a data breach of 5.4 million accounts
2022 has not been the best year for Twitter; from the problems it has had thanks to Elon Musk to breaches in its security, the little blue bird has been having a terrible few months. But that has not stopped its users from continuing to interact and share their thoughts. After all, in this network, […]
Dropbox credentials stolen with a resignation letter

We know that cybercriminals look every day for very creative ways to deceive users; in this way, they do not think that it is a fraud when they put their credentials on the pages they access. But, in this case, it is a resignation letter that is tricking many into handing over their Dropbox service […]
Elon Musk’s Twitter will offer end-to-end encryption in DMs

The shocking news this week was the purchase of the microblogging platform Twitter, by the CEO of SpaceX and Tesla, Elon Musk. News that impressed many due to the length of the negotiations. Despite knowing Elon’s work, there are many users concerned about the changes. However, one of the things he wants to change is […]
Ukrainian soldiers are hacked

You might think that cyberwarfare only targets large corporations and government agencies of the parties involved in the conflicts. It turns out that, in these modern times, a pattern is being noticed where groups attack and access people’s accounts. In this case, the Ukrainian soldiers were the latest victims of a Belarusian hacker group. Read […]
Businesses must follow these cloud data security practices

Today, many businesses place their processes and operations on the services offered by the cloud. There are many clouds out there, even from top-tier companies such as Google and Microsoft, but all of them present security problems to some degree. For that reason, it’s highly recommended that businesses follow cloud data security practices to protect […]
How Safe Are IoT Devices?

It is not so difficult to think that the future is already here when you see smart devices in any part of the home or office. They are called IoT devices, whose acronym stands for “Internet of Things.” These devices will always be connected to a network, providing constant access and communication between them. We […]
IT Professionals and Their Importance for Organizations

IT professionals have assumed great responsibilities over the years. Because, as the world moves into a digital age and everything is connected to a network, these professionals have become invaluable for everything to work properly. So, this article will show the importance of these professionals. Read: Meta Bans Seven “Cyber Mercenary” Companies The place of […]
Software Vulnerabilities Are Endless

Software vulnerabilities seem to have no end. Despite how much technology advances, hackers and cybercriminals adapt very well to changes, perfecting their techniques to find as many vulnerabilities as they can. Furthermore, every system will always have a vulnerability to exploit. Experts are always on the lookout for them. In this article, we will talk […]
Cybersecurity tips for Thanksgiving

In the United States, Thanksgiving is a major holiday, but these days can also be considered shopping dates in the American country. There are two days that quickly have become practically 2 weeks of big discounts and tons of shopping sprees: Black Friday and Cyber Monday. However, many customers prefer to make their purchases online, […]
Cybersecurity in Latin America: Strengths and weaknesses

Cybersecurity in Latin America is an important aspect that has been growing over the years. But, in these times that require stronger security in many different fields, Latin American countries are showing a desire to improve their security in the digital world. Today’s article will show the strengths and weaknesses of this region regarding cybersecurity. […]
Google is turning on the two-factor authentication for every user

The two-factor authentication has become a new layer of security for many systems and services. Still, the most recent one to implement it as a mandatory feature is Google, enrolling about 150 million users automatically before the year ends. There are some details about this change; keep reading to find out more! Read: GriftHorse is […]
