Security and Vulnerability Assessments

Our Partners

























Pen Test
Penetration testing goes beyond vulnerability scanning to use multistep and multivector attack scenarios that first find vulnerabilities and then attempt to exploit them to move deeper into the enterprise infrastructure. Since this is how advanced targeted attacks work, penetration testing provides visibility into aggregations of misconfigurations or vulnerabilities that could lead to an attack that could cause a serious business impact. As a minimum, penetration testing provides a means for prioritizing the highest-risk vulnerabilities.
Security / Risk Assessment
- Eagle Tech plans, develops and executes vulnerability scans of organization information systems
- Identifies and resolves false positive findings in assessment results
- Performs reconnaissance and information collection on the target environment or attack surface
- Identifies potential weaknesses and vulnerabilities on assets (i.e., end points, applications, users)
- Validates weaknesses via exploitation, and reports their findings
Governance and Data Validation
- Maintains and enhances the documentation standard for discoveries and reporting of malicious tactics, techniques and procedures
- Updates security policies and procedures
- Recommends security controls and/or corrective actions for mitigating technical and business risk
- Creates hypotheses for analytics and testing of threat data
- Analyzes data from threat and vulnerability feeds and analyzes data for applicability to the organization
Communication
- Generates reports on assessment findings and summarizes to facilitate remediation tasks
- Works with developers to advise on security needs and requirements
- Shares lessons learned, initial indicators of detection and opportunities for strengthening signature based detection capabilities
- Collects information from a wide variety of sources, and aggregates the information relevant to the company’s security environment
DO YOU KNOW WHAT’S ON YOUR IT NETWORK?
Most Businesses either don’t know how their IT network is vulnerable or isn’t using preventative technologies.
THE COST OF NOT KNOWING
REVENUE
The average SMB data breach costs thousands of dollars to remediate.
REPUTATION
59% of buyers avoid organizations that have experienced a cyberattack within the previous year.
REACH
Hackers target SMBs in hopes of breaching their customers’ data.
DO YOU KNOW WHERE MOST THREATS COME FROM?
Most data breaches start from within. Your own employees and contractors can unwittingly leave a backdoor open to cybercriminals.
33% of data breaches
are attributable to an internal employee or contractor.


THE NETWORK SECURITY THREAT LANDSCAPE IS EXPANDING
As large organizations improve their security posture through technology investments,
Small and Medium Businesses are becoming more
attractive targets to threat actors.
Small and Medium Businesses are less likely to invest in a comprehensive security posture that includes internal and external threat prevention.
GET IN THE GREEN
Go from zero visibility into IT network activity and performance to having all connected devices mapped and categorized as well as issues prioritized using a green-yellow-red rating system.
Confident that the network security is up to date and reliable?
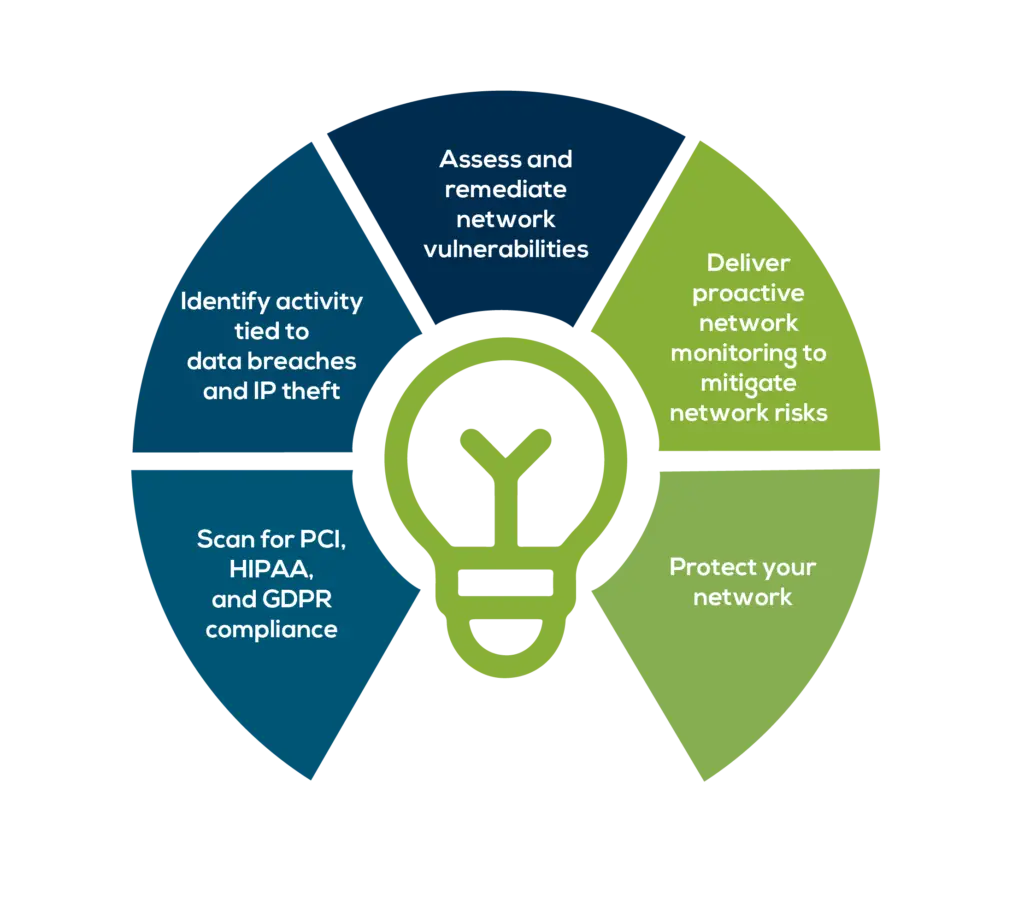
Risk Security assessments are essential for any organization that wants to protect its data, assets, and reputation from cyber threats. Eagle Tech Corp offers comprehensive and customized security and vulnerability assessments that help identify and mitigate the risks in the IT environment.
Whether the client needs a one-time assessment or a periodic review, Eagle Tech Corp can provide the best solutions and recommendations to enhance the security posture. Contact us today to schedule a consultation and learn how we can help to secure the future.
Some of our clients















